Previous Versions and Shadow Copies
Windows 7 can also restore earlier versions of files so that users can quickly recover a file that has been accidentally modified, corrupted, or deleted. Depending on the type of file or folder, users can open, save to a different location, or restore a previous version. The sections that follow describe the Volume Shadow Copy technology and the Previous Versions user interface.
How Volume Shadow Copy Works
To provide backups for files that are in use, Windows 7 uses the Volume Shadow Copy service, which was first introduced with Windows XP. Volume Shadow Copy mitigates file access between applications and the backup process. In other words, if a backup tool needs to access a file currently in use, Volume Shadow Copy creates a shadow copy of that file and then provides the backup process access to the shadow copy. Figure below illustrates the relationship between Volume Shadow Copy features.
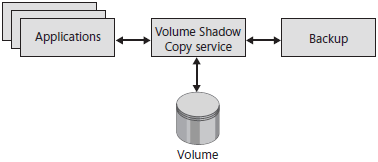
Volume Shadow Copy works with any application. Some applications, however, can communicate directly with the Volume Shadow Copy service to ensure that backed-up files are consistent. If an application keeps several files in use at the same time, they might become inconsistent if two files must be synchronized and one of those files is updated after another is backed up in an earlier state.
Note Application developers can build Volume Shadow Copy integration into their applications
using the Volume Shadow Copy Service software development kit (SDK). For more
information, go to
http://www.microsoft.com/downloads/details.aspx?FamilyID=0b4f56e4-0ccc-4626-826a-ed2c4c95c871.
To provide backup access to a file that is open and being updated, Volume Shadow Copy needs to be able to make two versions of the file accessible: one that is currently in use by the application and a second that is a snapshot of the file when backup first requested access to a volume shadow copy. Volume Shadow Copy handles this transparently by storing copies of changed files in Volume Shadow Copy storage. Volume Shadow Copy stores a copy of the original state of any modified portion of a file, which allows the original file to be updated without interrupting the backup process. In other words, if a user modifies a file after the backup starts, the file will be in the state it was in when the backup began.
In this tutorial:
- Managing Disks and File Systems
- Overview of Partitioning Disks
- How to Choose Between MBR or GPT
- Converting from MBR to GPT Disks
- GPT Partitions
- Choosing Basic or Dynamic Disks
- Working with Volumes
- How to Create a Simple Volume
- How to Create a Spanned Volume
- How to Create a Striped Volume
- How to Resize a Volume
- How to Delete a Volume
- How to Create and Use a Virtual Hard Disk
- File System Fragmentation
- Backup And Restore
- How File Backups Work
- File and Folder Backup Structure
- How System Image Backups Work
- How to Start a System Image Backup from the Command Line
- How to Restore a System Image Backup
- System Image Backup Structure
- Best Practices for Computer Backups
- How to Manage Backup Using Group Policy Settings
- Previous Versions and Shadow Copies
- How to Manage Shadow Copies
- How to Restore a File with Previous Versions
- How to Configure Previous Versions with Group Policy Settings
- Windows ReadyBoost
- BitLocker Drive Encryption
- How BitLocker Encrypts Data
- How BitLocker Protects Data
- TPM with External Key (Require Startup USB Key At Every Startup)
- TPM with PIN (Require PIN At Every Startup)
- TPM with PIN and External Key
- BitLocker To Go
- BitLocker Phases
- Requirements for Protecting the System Volume with BitLocker
- How to Enable the Use of BitLocker on the System Volume on Computers Without TPM
- How to Enable BitLocker Encryption on System Volumes
- How to Enable BitLocker Encryption on Data Volumes
- How to Manage BitLocker Keys on a Local Computer
- How to Manage BitLocker from the Command Line
- How to Recover Data Protected by BitLocker
- How to Disable or Remove BitLocker Drive Encryption
- How to Decommission a BitLocker Drive Permanently
- How to Prepare AD DS for BitLocker
- How to Configure a Data Recovery Agent
- How to Manage BitLocker with Group Policy
- The Costs of BitLocker
- Windows 7 Encrypting File System
- How to Export Personal Certificates
- How to Import Personal Certificates
- How to Grant Users Access to an Encrypted File
- Symbolic Links
- How to Create Symbolic Links
- How to Create Relative or Absolute Symbolic Links
- How to Create Symbolic Links to Shared Folders
- How to Use Hard Links
- Disk Quotas
- How to Configure Disk Quotas on a Single Computer
- How to Configure Disk Quotas from a Command Prompt
- How to Configure Disk Quotas by Using Group Policy Settings
- Disk Tools
- EFSDump
- SDelete
- Streams
- Sync
- MoveFile and PendMoves
