How BitLocker Encrypts Data
BitLocker encrypts entire volumes. The contents of the volumes can be decrypted only by someone with access to the decryption key, known as the Full Volume Encryption Key (FVEK). Windows 7 actually stores the FVEK in the volume metadata; this is not a problem because the FVEK itself is encrypted using the Volume Master Key (VMK).
Both the FVEK and the VMK are 256 bits. The FVEK always uses AES encryption to protect the volume. By editing the Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Choose Drive Encryption Method And Cipher Strength Group Policy setting, you can set the specific AES encryption strength to one of four values:
- AES 128 bit with Diffuser (this is the default setting)
- AES 256 bit with Diffuser (this is the strongest setting, but using it might negatively affect performance)
- AES 128 bit
- AES 256 bit
More Info For more information about the encryption algorithms used and the use of diffusers, read "AES-CBC + Elephant Diffuser: A Disk Encryption Algorithm for Windows Vista," at http://download.microsoft.com/download/0/2/3/0238acaf-d3bf-4a6d-b3d6-0a0be4bbb36e/BitLockerCipher200608.pdf.
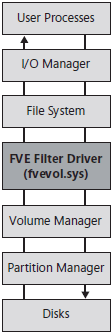
Windows Vista and Windows 7 encrypt and decrypt disk sectors on the fly as data is read and written (as long as it has access to the FVEK) using the FVE Filter Driver (Fvevol.sys). As shown in Figure below, the FVE Filter Driver, like all filter drivers, resides between the file system (which expects to receive the unencrypted contents of files) and the volume manager (which provides access to the volume). Therefore, applications and users are not aware of encryption when everything is functioning normally.
Encrypting and decrypting data do affect performance. While reading from and writing to a BitLocker-encrypted volume, some processor time will be consumed by the cryptographic operations performed by BitLocker. The actual impact depends on several factors, including caching mechanisms, hard drive speed, and processor performance. However, Microsoft has put great effort into implementing an efficient AES engine so that the performance impact on modern computers is minimal.
In this tutorial:
- Managing Disks and File Systems
- Overview of Partitioning Disks
- How to Choose Between MBR or GPT
- Converting from MBR to GPT Disks
- GPT Partitions
- Choosing Basic or Dynamic Disks
- Working with Volumes
- How to Create a Simple Volume
- How to Create a Spanned Volume
- How to Create a Striped Volume
- How to Resize a Volume
- How to Delete a Volume
- How to Create and Use a Virtual Hard Disk
- File System Fragmentation
- Backup And Restore
- How File Backups Work
- File and Folder Backup Structure
- How System Image Backups Work
- How to Start a System Image Backup from the Command Line
- How to Restore a System Image Backup
- System Image Backup Structure
- Best Practices for Computer Backups
- How to Manage Backup Using Group Policy Settings
- Previous Versions and Shadow Copies
- How to Manage Shadow Copies
- How to Restore a File with Previous Versions
- How to Configure Previous Versions with Group Policy Settings
- Windows ReadyBoost
- BitLocker Drive Encryption
- How BitLocker Encrypts Data
- How BitLocker Protects Data
- TPM with External Key (Require Startup USB Key At Every Startup)
- TPM with PIN (Require PIN At Every Startup)
- TPM with PIN and External Key
- BitLocker To Go
- BitLocker Phases
- Requirements for Protecting the System Volume with BitLocker
- How to Enable the Use of BitLocker on the System Volume on Computers Without TPM
- How to Enable BitLocker Encryption on System Volumes
- How to Enable BitLocker Encryption on Data Volumes
- How to Manage BitLocker Keys on a Local Computer
- How to Manage BitLocker from the Command Line
- How to Recover Data Protected by BitLocker
- How to Disable or Remove BitLocker Drive Encryption
- How to Decommission a BitLocker Drive Permanently
- How to Prepare AD DS for BitLocker
- How to Configure a Data Recovery Agent
- How to Manage BitLocker with Group Policy
- The Costs of BitLocker
- Windows 7 Encrypting File System
- How to Export Personal Certificates
- How to Import Personal Certificates
- How to Grant Users Access to an Encrypted File
- Symbolic Links
- How to Create Symbolic Links
- How to Create Relative or Absolute Symbolic Links
- How to Create Symbolic Links to Shared Folders
- How to Use Hard Links
- Disk Quotas
- How to Configure Disk Quotas on a Single Computer
- How to Configure Disk Quotas from a Command Prompt
- How to Configure Disk Quotas by Using Group Policy Settings
- Disk Tools
- EFSDump
- SDelete
- Streams
- Sync
- MoveFile and PendMoves
