Isolated Networks
Many organizations have networks that are separated into multiple security zones. Some networks have a high-security zone that is isolated because it has sensitive information, whereas other networks are separated from the core network because they are in a different physical location (branch office locations).
High-Security Zone
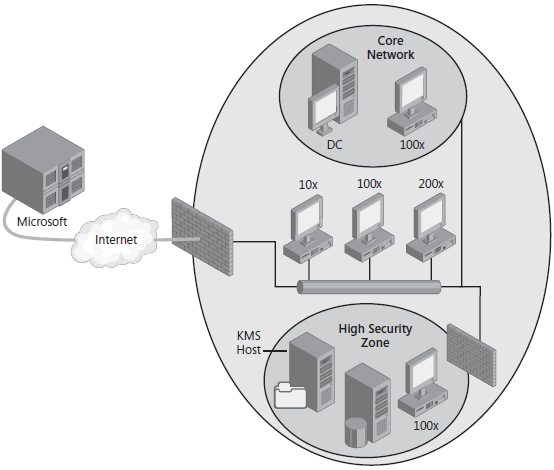
High-security zones are network segments separated by a firewall that limits communication to and from other network segments. If the computers in a high-security zone are allowed access to the core network by allowing TCP port 1688 outbound from the high-security zone and an RPC reply inbound, activate computers in the high-security zone by using KMS hosts located in the core network. This way, the number of client computers in the high-security network does not have to meet any KMS activation threshold.
If these firewall exceptions are not authorized and the number of total computers in the high-security zone is sufficient to meet KMS activation thresholds, add a local KMS host to the high-security zone. Then, activate the KMS host in the high-security zone by telephone.
Figure below shows an environment with a corporate security policy that does not allow traffic between computers in the high-security zone and the core network. Because the highsecurity zone has enough computers to meet the KMS activation threshold, the high-security zone has its own local KMS host. The KMS host itself is activated by telephone.
If KMS is not appropriate because there are only a few computers in the high-security zone, MAK Independent activation is recommended. Each computer can be activated independently with Microsoft by telephone.
MAK Proxy activation using VAMT is also possible in this scenario. VAMT can discover client computers by using AD DS, computer name, IP address, or membership in a workgroup. VAMT uses WMI to install MAK product keys and CIDs and to retrieve status on MAK clients. Because this traffic is not allowed through the firewall, there must be a local VAMT host in the high-security zone and another VAMT host in another zone that has Internet access.
In this tutorial:
- Using Volume Activation
- Introduction Volume Activation
- Activation Options
- Volume Licensing
- Key Management Service
- How KMS Works
- Client Discovery of the KMS
- Planning a KMS Deployment
- Planning DNS Server Configuration
- Upgrading Existing KMS Hosts
- Multiple Activation Key
- Volume Activation Management Tool
- Volume Activation Scenarios
- Core Network
- Isolated Networks
- Branch Office Locations
- Individual Disconnected Computers
- Test/Development Labs
- What If Systems Are Not Activated?
