How the Protected Mode Compatibility Layer Works
To minimize the impact of the strict security restrictions, Protected Mode provides a compatibility architecture that redirects some requests to protected resources and prompts the user to approve other requests. Figure below illustrates this behavior.
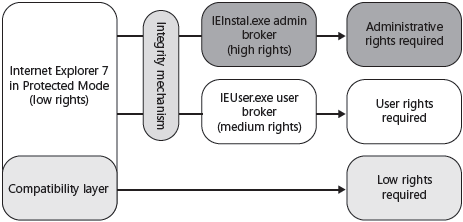
The compatibility layer handles the needs of extensions written for earlier versions of Windows that require access to protected resources by redirecting the requests to safer locations. Specifically, the Documents folder is redirected to \%UserProfile%\AppData\Local \Microsoft\Windows\Temporary Internet Files\Virtualized, and the HKEY_CURRENT_USER registry hive is redirected to HKEY_CURRENT_USER\Software\Microsoft\InternetExplorer \InternetRegistry.
The first time an add-on attempts to write to a protected object, the compatibility layer copies the object and then modifies the copy. After the first modification is made, the compatibility layer forces add-ons to read from the copy. The Internet Explorer compatibility layer virtualization is used instead of the Windows Vista and later operating systems UAC virtualization.
Note A dd-ons developed for Windows Vista and later operating systems can bypass the compatibility layer to save a file by calling the SaveAs application programming interface (AP I), so no functionality is lost. To allow the user to select a location to save a file, call IEShowSaveFileDialog to prompt the user for a folder and then call IESaveFile to write the file. Use IEGetWriteableFolderPath and IEGetWriteableHKCU to find low-integrity locations to which your add-on can write. To determine whether Protected Mode is active, call the IEIsProtectedModeProcess method. For more information, visit http://msdn.microsoft.com/en-us/library/ms537319.aspx.
Two higher-privilege broker processes allow Internet Explorer and extensions to perform elevated operations given user consent:
- The User Broker (IEUser.exe) process provides a set of functions that lets the user save files to areas outside of low-integrity areas.
- The Admin Broker (IEInstal.exe) process allows Internet Explorer to install ActiveX controls.
In this tutorial:
- Managing Windows Internet Explorer
- Internet Explorer 8 Improvements
- InPrivate Browsing
- InPrivate Filtering
- Compatibility View
- SmartScreen
- Domain Highlighting
- Tab Isolation
- Accelerators
- Improvements Previously Introduced in Internet Explorer 7
- User Interface Changes
- Tabbed Browsing
- Search Bar
- How to Create a Web Link to Add a Custom Search Provider
- How to Configure Custom Search Providers Using the Registry
- How to Configure Custom Search Providers Using Group Policy
- RSS Feeds
- Improved Standards Support
- Expanded Group Policy Settings
- Defending Against Malware
- How Protected Mode Improves Security
- How the Protected Mode Compatibility Layer Works
- How to Solve Protected Mode Incompatibilities
- URL-Handling Protection
- Address Bar Visibility
- Cross-Domain Scripting Attack Protection
- Controlling Browser Add-ons
- Add -on Manager Improvements
- Protecting Against Data Theft
- Security Status Bar
- How the Smart Screen Filter Works
- How to Configure Smart Screen Options
- Deleting Browsing History
- Blocking IDN Spoofing
- Security Zones
- Understanding Zones
- Configuring Zones on the Local Computer
- Configuring Zones Using Group Policy
- Network Protocol Lockdown
- Managing Internet Explorer Using Group Policy
- Group Policy Settings for Internet Explorer 7 and Internet Explorer 8
- New Group Policy Settings for Internet Explorer 8
- Using the Internet Explorer Administration Kit
- Troubleshooting Internet Explorer Problems
- Internet Explorer Does Not Start
- An Add-on Does Not Work Properly
- Some Web Pages Do Not Display Properly
- Preventing Unwanted Toolbars
- The Home Page or Other Settings Have Changed
