Understanding the Windows Filtering Platform
The Windows Filtering Platform (WFP) is an architectural feature of Windows Vista and later versions that allows access to Transmission Control Protocol/Internet Protocol (TCP/ IP) packets as they are being processed by the TCP/IP networking stack. WFP is the engine that implements packet-filtering logic, and it is accessible through a collection of public APIs which provide hooks into the networking stack and the underlying filtering logic upon which Windows Firewall is built. Independent Software Vendors (ISVs) can also use WFP to develop third-party firewalls, network diagnostic software, antivirus software, and other types of network applications. Using these APIs, a WFP-aware filtering application can access a packet anywhere in the processing path to view or modify its contents. Third-party vendors and network application developers should utilize the WFP APIs only for filtering applications or security applications.
As shown in Figure below, the main features of the WFP are as follows:
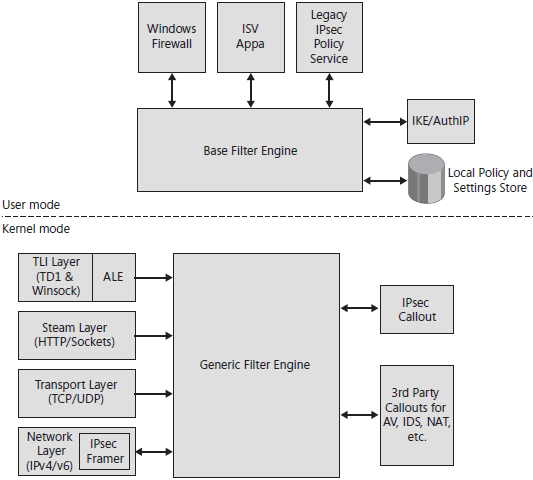
- Base Filter Engine The Base Filter Engine (BFE) runs in user mode and receives filtering requests made by Windows Firewall, third-party applications, and the legacy IPsec policy service. The BFE then plumbs the filters created by these requests into the Kernel Mode Generic Filter Engine. The BFE (Bfe.dll) runs within a generic SvcHost.exe process.
- Generic Filter Engine The GFE receives the filters plumbed from the BFE and stores them so that the different layers of the TCP/IP stack can access them. As the stack processes a packet, each layer the packet encounters calls the GFE to determine whether the packet should be passed or dropped. The GFE also calls the various callout modules (defined next) to determine whether the packet should be passed or dropped. (Some callouts may perform an identical function, especially if multiple third-party firewalls are running concurrently.) The GFE (Wfp.lib) is part of the Kernel Mode Next Generation TCP/IP Stack (NetioTcpip.sys) first introduced in Windows Vista. The GFE is actually the Kernel Mode enforcement engine portion of the BFE and is not a separate feature.
- Callout modules These features are used for performing deep inspection or data modification of packets being processed by the pack. Callout modules store additional filtering criteria that the GFE uses to determine whether a packet should be passed or dropped.
Note The BFE can support multiple clients simultaneously. This means that a third-party, WFP-aware application can interact with and even override Windows Firewall with Advanced Security if so designed.
The APIs of the BFE are all publicly documented so that ISVs can create applications that hook into the advanced filtering capabilities of the Next Generation TCP/IP Stack in Windows Vista and later versions. Some of the filtering features of the WFP are implemented using callouts, but most filtering is performed using static filters created by the BFE as it interacts with Windows Firewall. The Windows Firewall service monitors the system to make sure the filters passed to BFE reflect the environment of the system at any given time. These public WFP APIs are scriptable and expose the full configurability of Windows Firewall, but they have some limitations, such as no support for IPsec integration.
In this tutorial:
- Configuring Windows Firewall and IPsec
- Understanding Windows Firewall with Advanced Security
- Improvements to Windows Firewall Introduced Previously in Windows Vista
- Additional Improvements to Windows Firewall in Windows 7
- Understanding the Windows Filtering Platform
- Windows Firewall and the Startup Process
- Understanding Windows Service Hardening
- Understanding Service SIDs
- Windows Firewall and WSH
- Windows Firewall and Service Triggers
- Understanding Multiple Active Firewall Profiles
- Understanding Rules
- Understanding Firewall Rules
- Inbound vs . Outbound Rules
- Allow vs . Block Rules
- Allow If Secure Rules
- Authenticated Bypass Rules
- Filtering Conditions FOR Firewall RULES
- Understanding Connection Security Rules
- Types of Connection Security Rules
- Supported IPsec Settings for Connection Security Rules
- Default IPsec Settings for Connection Security Rules
- Windows Firewall and Windows PE
- Understanding Default Rules
- Understanding WSH Rules
- Understanding Rules Processing
- Managing Windows Firewall with Advanced Security
- Tools for Managing Windows Firewall with Advanced Security
- Managing Windows Firewall Using Control Panel
- Managing Windows Firewall Using the Windows Firewall with Advanced Security Snap-in
- Managing Windows Firewall Using Group Policy
- Considerations When Managing Windows Firewall Using Group Policy
- Managing Windows Firewall Using the Netsh Command
- Common Management Tasks
- Enabling or Disabling Windows Firewall
- Configuring Firewall Profiles and IPsec Settings by Using Group Policy
- Creating and Configuring Firewall Rules
- Creating and Configuring Connection Security Rules
- Monitoring Windows Firewall
- Troubleshooting Windows Firewall
- Troubleshooting Windows Firewall Using Firewall Logs
- Troubleshooting Windows Firewall Using Event Logs
- Troubleshooting Windows Firewall Using Auditing
- Troubleshooting IPsec Issues Using Netsh Wfp
- Troubleshooting Windows Filtering Platform and IPsec Issues Using Netsh Trace
