Tunnel and Transport Mode
IPsec defines two modes for exchanging secured data: tunnel mode and transport mode. IPsec transport mode protects upper-layer protocols and is used between end nodes. This approach allows end-to-end security because the host originating the packet is also securing it, and the destination host is able to verify the security, either by decrypting the packet or certifying the authentication.
Tunnel mode IPsec protects the entire contents of the tunneled packets. The tunneled packets are accepted by a system acting as a security gateway, encapsulated inside a set of IPsec/IP headers, and forwarded to the other end of the tunnel, where the original packets are extracted (after being certified or decrypted) and then passed along to their ultimate destination.
The packets are only secured as long as they are " inside " the tunnel, although the originating and destination hosts could be sending secured packets themselves, so that the tunnel systems are encapsulating packets that have already been secured.
Transport mode is good for any two individual hosts that want to communicate securely; tunnel mode is the foundation of the Virtual Private Network , or VPN . Tunnel mode is also required any time a security gateway (a device offering IPsec services to other systems) is involved at either end of an IPsec transmission. Two security gateways must always communicate by tunneling IP packets inside IPsec packets; the same goes for an individual host communicating with a security gateway. This occurs any time a mobile laptop user logs into a corporate VPN from the road, for example.
Tunneling allows two systems to set up SAs to enable secure communications over the Internet. Network traffic originates on one system, is encrypted and/or signed, and is then sent to the destination system. On receipt, the datagram is decrypted or authenticated, and the payload is passed along up the receiving system's network stack where it is finally processed by the application using the data. This is a transparent mode use of security associations, because the two hosts could be communicating just as easily without security headers-and because the actual IP headers of the datagrams must be exposed to allow them to be routed across the Internet.
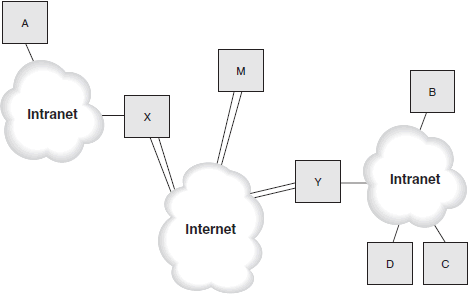
An SA can also be used to tunnel secure IP through an internetwork. Figure below shows how this works. All IP packets from system A are forwarded to the security gateway X, which creates an IP tunnel through the Internet to security gateway Y, which unwraps the tunneled packets and forwards them. Security gateway Y might forward those packets to any of the hosts (B, C, or D) within its own local intranet, or it could forward them to an external host, like M. It all depends on where the originating host directs those packets. Whenever an SA destination node is a security gateway, it is by definition a tunneled association. In other words, tunneling can be done between two security gateways (as shown in Figure below ), or it can be done between a regular node and a security gateway. Thus, host M could create a tunneled connection with either security gateway, X or Y. It is tunneled by virtue of the fact that datagrams sent from M are passed fi rst to the security gateway, which then forwards them appropriately after decrypting or authenticating.
In this tutorial:
- IP Security
- IP Security Issues
- Security Goals
- Encryption and Authentication Algorithms
- Symmetric Encryption
- Public Key Encryption
- Key Management
- Secure Hashes
- Digital Signature
- IPSEC: The Protocols
- IP and IPSEC
- Security Associations
- Using Security Associations
- Tunnel and Transport Mode
- Encapsulating Security Payload (ESP)
- Authentication Header
- Calculating the Integrity Check Value (ICV)
- IPsec Headers in Action
- Implementing and Deploying IPSEC
