The Link Layer
Also known as the host-to-network layer, data link layer or network access layer.
This covers both the hardware of the OSI physical layer and the software in the OSI data link layer. The TCP/IP model does not say much about this layer as it recognizes that there can be many different types of hardware to send your packets across. This layer has to be capable only of sending and receiving IP packets.
The Network Layer
Also known as the Internet layer. This handles the movement of packets about the network, including routing. This layer defines a specific packet format and a protocol, the Internet Protocol (IP), to manipulate those packets (Figure below).
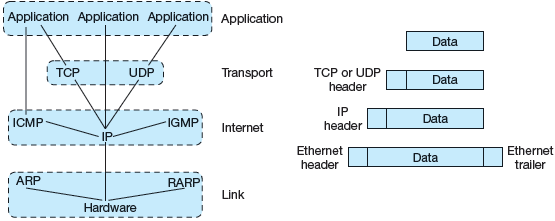
The Transport Layer
Also known as the host-to-host layer. This is analogous to the OSI transport layer. It provides for a flow of data between source and destination. Two protocols are defined at this level, TCP and UDP.
The Transmission Control Protocol (TCP) is a reliable connection-oriented protocol that delivers a stream of bytes from source to destination. It chops the incoming byte stream into packets and passes them to the Internet layer. It copes with acknowledgement packets and resends packets if it thinks they have been lost. Going the other way, it receives packets and reassembles them into a continuous byte stream, sending acknowledgements for successfully received packets. Flow control is also handled here.
The User Datagram Protocol (UDP) is an unreliable, connectionless protocol for those cases where you do not want TCP's overhead or do not require its reliability. UDP is used for situations where fast delivery is preferred to accurate delivery, e.g., sound or video.
The world 'unreliable' is being used in a technical sense here as meaning 'not guaranteed reliable'. Many typical unreliable networks are actually pretty reliable these days.
Theoretically, TCP and UDP should not have to be layered on top of IP, but their specifications actually tie them into IP. This is breaking the principle of layering but TCP/IP was designed before the concept of layering was recognized as important.
The TCP checksum includes some fields from the IP layer in a straightforward violation of the layering precept.
The Application Layer
The next layer is the application layer, which provides protocols like SMTP, FTP and telnet. This model does not have session or presentation layers.
Unfortunately, presentation is important so applications have to cope with presentation issues themselves, e.g., by using libraries like XDR to convert data to a machine-independent form. You can try to avoid the worst problems by sticking to a tightly restricted subset of values such as the ASCII character set. Even then occasional glitches do occur, such as Web pages generated by some tools which use fancy nonstandard characters where simple characters were all that was required. This is due to these tools not following generally accepted standards. The result is Web pages that look fine on some browsers, but can be unreadable on other browsers.
The Internet model is somewhat more flexible than the OSI one. Applications can (in rare cases) use the network layer directly (IP and ICMP) rather than going through TCP or UDP. This appears to contradict the point of using layers, but (a) it is convenient and (b) since we are talking about IP we already know what the lower layers look like and they are unlikely to change often. We shall have to pay the price if there is a change: a case in point is the introduction of IPv6, the next version of the IP. For the overwhelming majority of cases applications do use TCP or UDP. This kind of pragmatism is common when the Internet is involved.
In this tutorial:
- Layering Models
- The Seven Layer Model
- The Physical Layer
- The Data Link Layer
- The Network Layer
- The Transport Layer
- The Session Layer
- The Presentation Layer
- The Application Layer
- How the Layers Fit Together
- Why Layers and Encapsulation?
- The Internet Model
- The Link Layer
- Models and Protocols
- Comparing OSI and Internet Models
